МНОГОФУНКЦИОНАЛЬНАЯ МОБИЛЬНАЯ БИОМЕТРИЯ ПО ОТПЕЧАТКУ ПАЛЬЦА И ДИНАМИКИ РУКОПИСНОЙ ПОДПИСИ
МНОГОФУНКЦИОНАЛЬНАЯ МОБИЛЬНАЯ БИОМЕТРИЯ ПО ОТПЕЧАТКУ ПАЛЬЦА И ДИНАМИКИ РУКОПИСНОЙ ПОДПИСИ
Научная статья
Серикова Ю.И.1, *, Князев В.Н.2
1 ORCID: 0000-0002-4959-321Х;
1, 2 Пензенский государственный университет, Пенза, Россия
* Корреспондирующий автор (julia-ska[at]yandex.ru)
АннотацияАвторами предлагается многофункциональная мобильная биометрия по совмещенным статическим и динамическим характеристикам человека. В качестве биометрических характеристик выступают отпечаток пальца и динамика рукописной подписи. Предлагаемая система относится к мультимодальным и состоит из модуля захвата данных, модуля извлечения функций и их объединения и модуля сравнения и принятия решения.
Научная новизна. Впервые в преобразователе биометрия-код используются сети квадратичных форм, извлечение биометрических характеристик идет последовательно, а их преобразование параллельно, образуя единый код доступа. При обработке сложных биометрических данных возникают ошибки второго рода весьма значительные и для их компенсации авторами предлагается переход из пространства обычных кодов в 2256 состояний в более компактное пространство расстояний Хэмминга. За счет этого достигается оптимальное соотношение ошибок первого и второго рода.
Ключевые слова: биометрия, глубокие нейронные сети, нечеткие экстракторы, сети квадратичных форм, преобразование Фурье, ошибки первого рода, ошибки второго рода, расстояние Хэмминга.
MULTIFUNCTIONAL MOBILE BIOMETRICS USING HUMAN FINGERPRINT AND DYNAMICS OF HANDWRITTEN SIGNATURE
Research article
Serikova Yu.I.1, *, Knyazev V.N.2
1 ORCID: 0000-0002-4959-321Х;
1, 2 Penza State University, Penza, Russia
* Corresponding author (julia-ska[at]yandex.ru)
AbstractThe authors propose multifunctional mobile biometrics based on combined static and dynamic characteristics of a person. The biometric characteristics are the fingerprint and the dynamics of the handwritten signature. The proposed system is multimodal and consists of a data capture module, a function extraction module and their combination, and a comparison and decision module.
Scientific novelty. For the first time in a biometrics-code converter, networks of quadratic forms are used, the extraction of biometric characteristics is carried out sequentially, and their transformation is carried out in parallel, forming a single access code.When processing complex biometric data, the arising errors of the second kind are very significant and to compensate them, the authors propose a transition from the space of ordinary codes in 2256 states to a more compact space of Hamming distances, due to which the optimal ratio of errors of the first and second kind is achieved.
Keywords: biometric, deep neural networks, fuzzy extractors, networks of quadratic forms, Fourier series, FAR, FRR, Hamming distance.
Today biometrics is an integral part of the global information technology market and is used as a convenient, reliable and innovative mechanism to ensure information security by recognizing the unique biometric characteristics inherent in an individual form to each person. According to the forecast «J`son & Partners Consulting» [1], the global market for information technology will reach US 40 billion dollars as early as 2022 (Fig. 1).
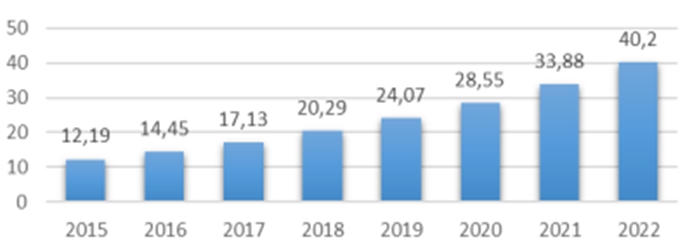
Fig. 1 – Volume of the world information technology market by 2015-2022
A similar situation is expected in the Russian market. The widespread use and possibilities of mobile technologies have shaped the need for people to lead their lives in constant motion. To meet this need, applications installed on mobile devices and tablets, and all kinds of transactions processed by them, must be protected. Therefore, we believe that special attention should be paid to the consideration of multifunctional mobile biometrics.
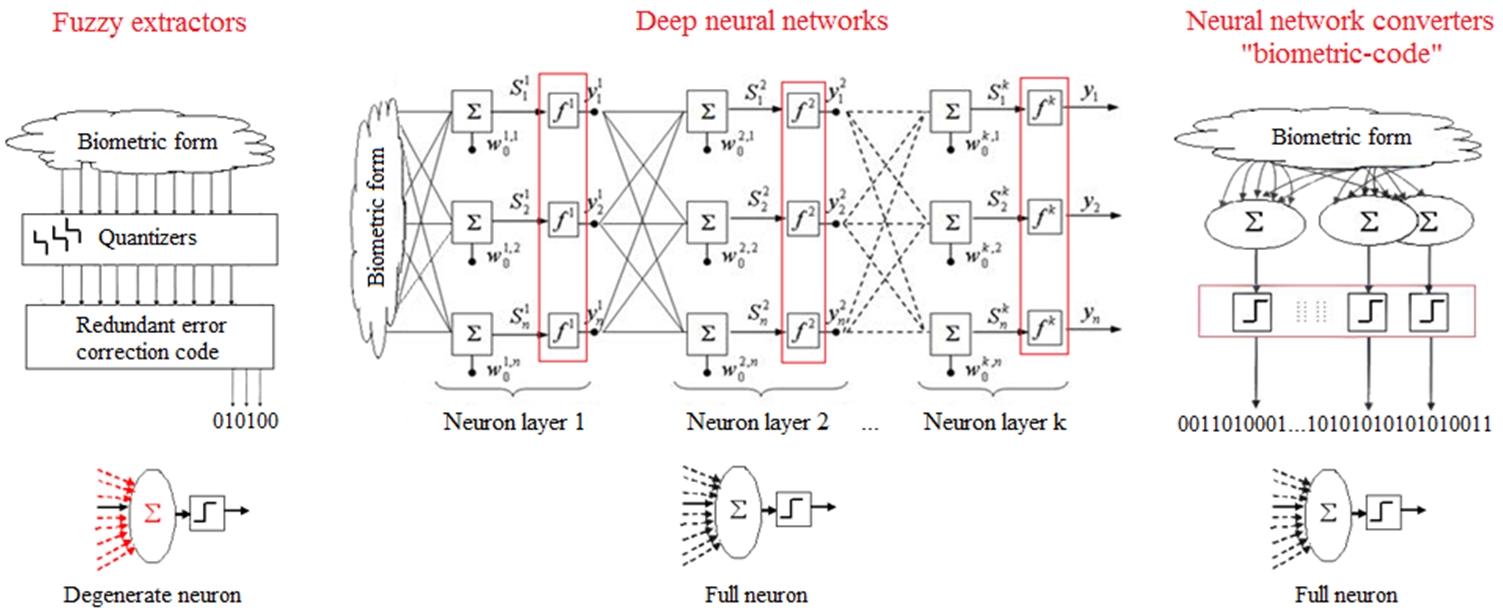
Multifunctional mobile biometrics belongs to the class of multimodal biometric systems used on mobile devices and tablets. Previously, we were faced with insufficient computing power of these devices, so the integration of several biometric modalities was impractical, now we have reached a new scientific and technical level. To date, there are 3 clusters of biometric data processing methods (Fig. 2): fuzzy extractors, deep neural networks and neural network converters biometrics-code.
Fig. 2 – Biometric data processing methods
Overview and comparative analysis of the advantages and disadvantages of biometric data processing methods show in tables 1-3.Table 1 – Comparative analysis of the advantages and disadvantages of fuzzy extractors
| Advantages | Disadvantages |
| 1. Training of a neural network on image of stranger (biometric form «Alien») is not required. 2. Ease of implementation of the biometric systen in practice. | 1. When processing data, the parameters of feature distribution are not taken into account. 2. Error-correcting codes are very redundant. 3. There is a strong vulnerability to tampering with an access key relative to other methods. 4. «Raw data» quantization (so the higher false acceptance rate (FAR) and false rejection rate (FRR)). |
Table 2 – Comparative analysis of the advantages and disadvantages of deep neural networks
| Advantages | Disadvantages |
| 1. Saving network memory (elastic fixing of weights). 2. Possibility of accurate forecasting. 3. High recognition accuracy and partial resistance to changes in scale, displacement, rotation, change of perspective and other distortions. | 1. Requires large computing resources. 2. Overfitting problem. 3. Linear subdivision of own regions. |
Table 3 – Comparative analysis of the advantages and disadvantages of neural network converters «biometric-code»
| Perceptrons and their modifications (GOST R 52633.5-2011) | |
| Advantages | Disadvantages |
| 1. Data enrichment 2. Biometric reference masking 3. The presence of a secure neural network container 4. Effective filtering of noise | 1. Network training is required on the «Alien» samples. 2. There is a need to store databases «Own» and «Alien». 3. Linear subdivision of own regions. |
| Quadratic form networks | |
| Advantages | Disadvantages |
| 1. Does not require large computing resources and does not require network training on the samples of «Alien». 2. Data enrichment and non-linear separation of eigenvalues of standards in the feature space. 3. Possibility of accurate forecasting. 4. Masking the biometric reference and the presence of a secure neural network container. 5. It is possible to isolate neurons to encrypt data multiple times, which in turn strengthens the protection of the network weights. 6. Effective noise filtering and mobility of use. | 1. Storing the parameters of the distribution of feature values (but in encrypted form). 2. Instability of output codes. |
Different requests may require different authentication, including recommendations to increase user experience when requesting access to sensitive information. But, since mobile devices and tablets are used by people in various conditions, usually not controlled, we recommend using static and dynamic characteristics of a person as biometric characteristics in multifunctional mobile biometrics to ensure reliability. Let us demonstrate the operation of such a system using the example of two biometric characteristics: a fingerprint and the dynamics of a handwritten signature (Fig. 3). Initially, it was planned to use deep neural networks [3], since they have proven themselves well in fingerprint recognition. However, attempts to use deep neural networks to solve the problem of recognition based on the dynamics of a handwritten signature did not justify the desired effect, and a number of fundamental shortcomings were revealed in the joint recognition of the «symbiosis» of static and dynamic characteristics:
- The algorithm for training deep neural networks «backpropagation of the error» has exponential computational complexity; it cannot be implemented on a tablet that does not have access to Google's network training servers (which is not acceptable in highly reliable biometric authentication applications).
- The existing algorithms for training (retraining) deep neural networks require a huge database (about 100,000 or more training examples), which is not mobile and resource-intensive.
- Modern deep neural networks, which provide high-quality recognition, have up to 100 layers of neurons, which is extremely redundant according to Kolmogorov's theorems [4].
- Users of authentication systems based on deep neural networks cannot be sure of the reliability of their work, since they do not have methods for quickly detecting FAR and FRR errors (for this reason, the developers of this technology have to come up with other criteria for assessing the reliability of networks, which, in turn, does not allow the implementation of such systems on a mobile device or tablet).
- Training of deep neural networks cannot be fully automated and is always carried out under human control, which is unacceptable in applications of highly reliable biometric authentication.
Fig. 3 – Multifunctional mobile biometric
Based on the above, it was decided to use quadratic form networks as a method for processing biometric information.
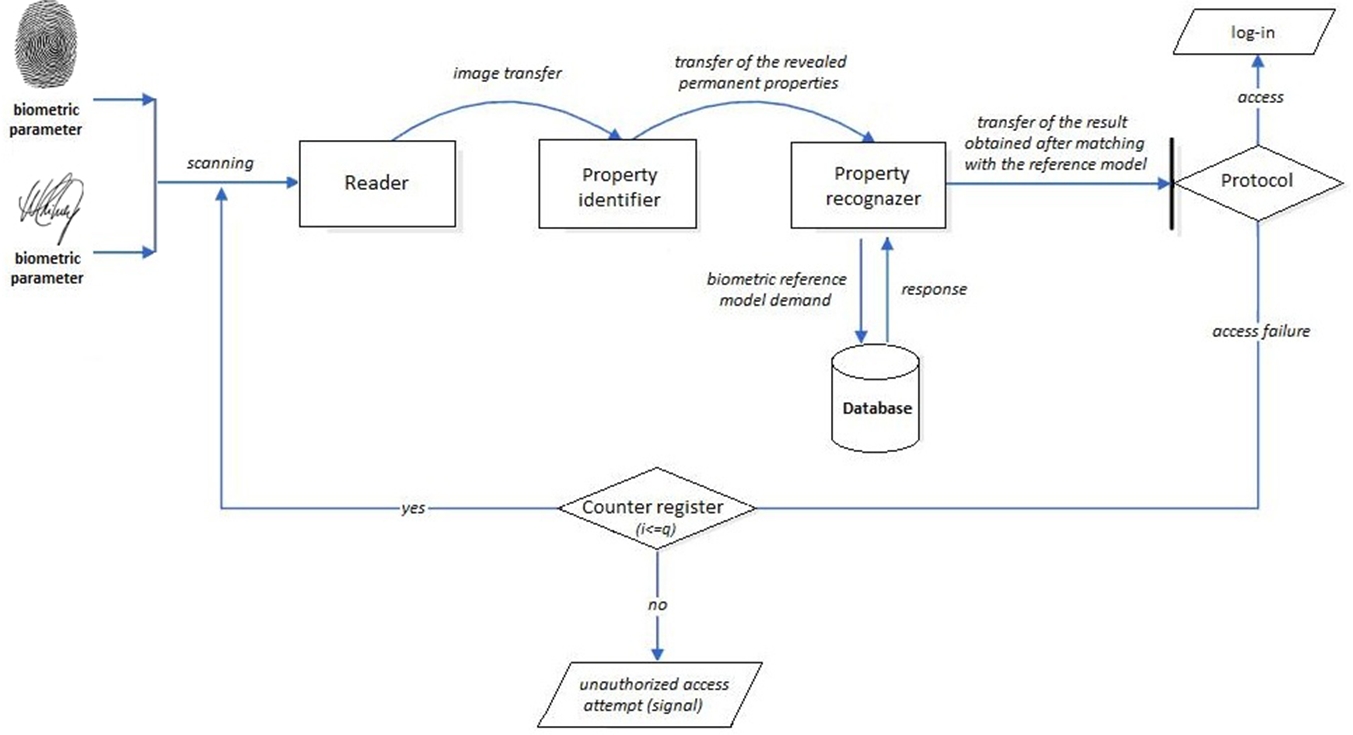
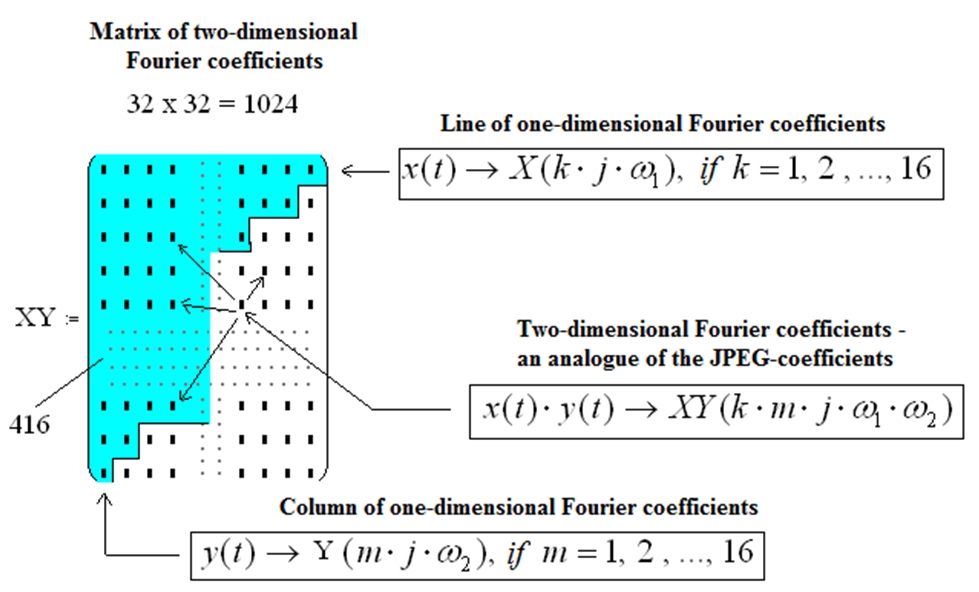
The authentication process [5], including its complexity, is developed in accordance with the request of users of multifunctional mobile biometrics.The system will consist of the following modules: Reader (Data Capture Module), Property Identifier (Function Extraction and Combining Module) and Property recognazer (Comparison and Decision Module). The quality of image recognition by the system, namely its neural network part - the biometrics-code converter, depends on the size of the space of primary and secondary biometric characteristics. Processing and extraction of primary characteristics will occurs in the Reader. The number of primary characteristics (raw biometric data) depends on the capabilities of the system hardware and is determined by the number of degrees of freedom, which describes the number of quasi-continuous characteristics. Extraction of biometric characteristics: fingerprint and signature dynamics goes sequentially from sensors to the Reader. For the formation of secondary characteristics, the obtained primary raw data will be will be parallelly used, which will undergo a discrete Fourier transform (Fig. 4) for the spectra of each of the parameters, followed by the extraction of their harmonic amplitudes and then undergo the data normalization procedure.
Fig. 4 – Discrete decomposition of biometric parameters in a Fourier series into coefficients
The formation of secondary characteristics and their normalization will occurs in the Property Identifier, at the output we will receive two vectors of controlled parameters, using the procedure – boost, we will create a symbiosis of biometric sampling (we will not combine two vectors into a new neural network container, we will generate a pair of iterators (range) which will cover the range of both containers). We need this in order to increase the reliability of the access code. By encompassing the range of both containers, we can impose certain conditions on the given range to label the biometric form «Own». So, if the first part of the generated access code has a threshold deviation of 10% from the original biometric form «Own», the system will also consider this image as own object (this allows us to deal with the shortcomings of fingerprint processing when it is injured). If we combined two vectors into a new neural network container and imposed a similar condition on it, we would change the entire access code, not part of it, and this would be followed by an incorrect biometric form «Own», which, according to statistics, could belong to the biometric form «Alien».The resulting code in the Property Identifier is a Biometric sample. The property recognizer will then compare the biometric sample declared in the system with the biometric reference stored in the Database (Fig. 5). If the result is positive, the system makes a decision on the user's admission, if the result is negative, access is.
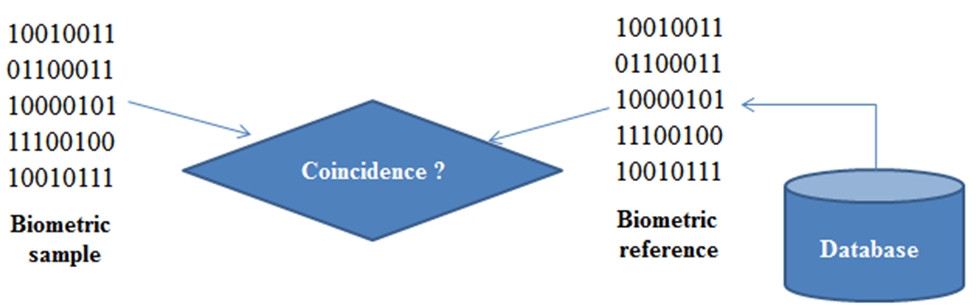
Fig. 5 – Comparison of Biometric sample declared to the system with Biometric reference stored in Database
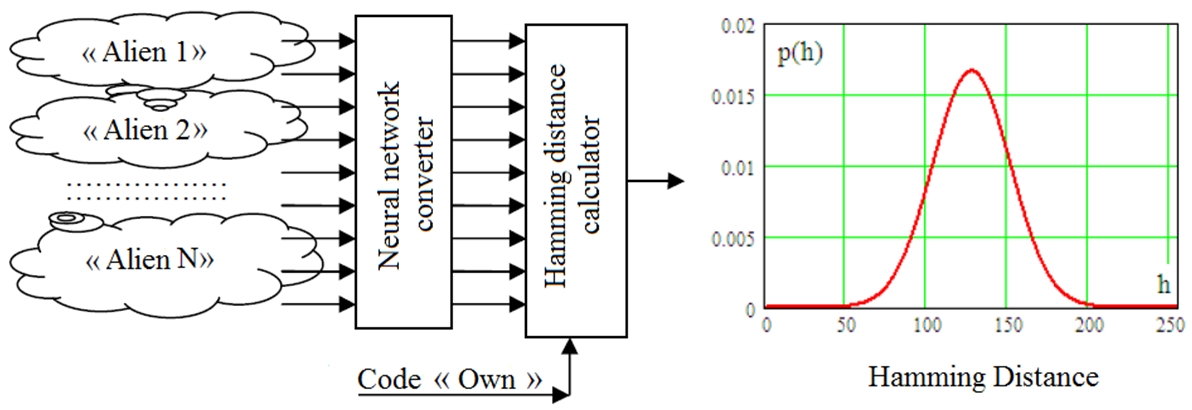
Each neuron in the neural converter looks at the presented biometric image from its own perspective in its dimension. The more in the neural network transducer, the more reliably it is able to distinguish the biometric form «Own» from the biometric form «Alien» or the biometric form «All aliens». When using a neural network of 256 neurons, the FAR is extremely small. To assess the FRR by conventional methods, it is required to create test databases of biometric formations of a very large size. We propose a transition from the spaces of ordinary codes 2256 to the more compact space of Hamming distances:
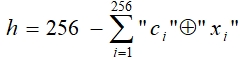 (1)
(1)
where ci - the bit of the code «Own»;
xi - the bit of the code «Alien».
This transition leads to a significant decrease in the requirements for the size of the test sample. Simplification of calculations is due to the fact that Hamming convolution (1) is a good FRR normalizer. FRR estimation by neural network converter show in the Figure 6.
Fig. 6 – FRR estimation by neural network converter
The obtained sample of Hamming distances allows calculating the mathematical expectation - E(h) and standard deviation - σ(h). With this data, we can roughly determine the FRR:
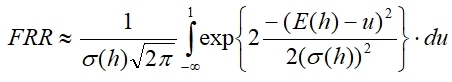 (2)
(2)
The probability of a complete match between code «Own» and code «Alien» h=0 is estimated as the probability of hitting in the interval from [-∞ ;1] continuous normal distribution, which is redundant. That is, estimate (2) is an upper bound for the probability of FAR. The transition to the Hamming distance space makes it possible to estimate the entropy of long codes (full-fledged neurons not degenerate). In this case, the entropy can be calculated both in the space of ordinary Hamming distances, and in the space of Hamming convolutions modulo 256 [6]. Listing of the MathCAD program show in the Figure 7. The expediency of switching to Hamming convolutions modulo 256 is because the encoding of texts in Russian and English is carried out in the ASCII standard (8 code bits per text character).
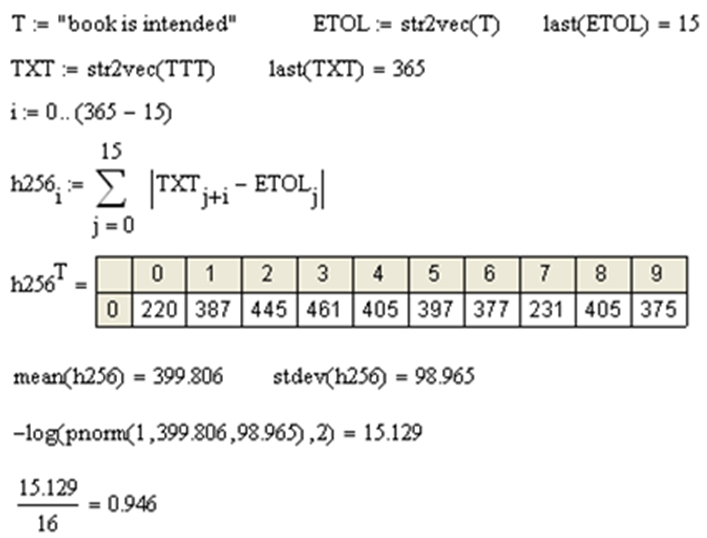
Fig. 7 – Calculation of the entropy of the code in the space of Hamming convolutions modulo 256
It turns out that the meaningful characters of the text must be compared with each other in the metric of 256 states (the number of states is 8 bits of the code).
Conclusion
Based on the results of the analysis of the biometric technologies market, taking into account information security and the volume of processed data, neural network converters «biometrics-code» was chosen as a biometric data processing method, and fingerprint biometrics and handwriting dynamics used as biometric characteristics. The FAR and FRR errors are fundamentally unremovable and we can only talk about reducing their probability to practically acceptable values. Since the error statistics are determined by the testing technique and duration, the volume and nature of statistical samples, the error probabilities are not only a function of the reliability of the method (statistically justified probability of the coincidence of characteristics in different people), but also a whole range of operating conditions. This is achieved through transition from the spaces of ordinary codes 2256 to the more compact space of Hamming distances.
| Конфликт интересов Не указан. | Conflict of Interest None declared. |
Список литературы / References
- Крылова, И. Ю. Биометрические технологии как механизм обеспечения информационной безопасности в цифровой экономике / И. Ю. Крылова, О. С. Рудакова. // Молодой ученый. — 2018. — № 45 (231). — С. 74-79.
- ГОСТ Р 52633.5-2011. Защита информации. Техника защиты информации.Автоматическое нейросетевых преобразователей биометрия-код доступа. – М.: Стандартинформ, 2011 – 20 с.
- Третье поколение нейросетей: "Глубокие нейросети" — [Электронный ресурс]. URL: https://www.mqlcom/ru/articles/1103 (дата обращения: 10.05.2021).
- Колмогоров А.Н. О представлении непрерывных функций нескольких переменных в виде суперпозиции непрерывных функций одного переменного / А.Н. Колмогоров // Докл. АН СССР. 1957. № 5 (114). C. 953–956.
- Серикова Ю. И. Актуальные проблемы безопасности биометрических систем аутентификации / Ю. И. Серикова, В. Н. Князев // Международный научно-исследовательский журнал. — 2016. — № 4 (46) Часть 2. — С. 177—182. — DOI: 10.18454/IRJ.2016.46.105.
- Иванов А.И. Численная оценка показателей квантовой сцепленности выходных кубит нейросетевой молекулы преобразователя биометрических данных / А.И. Иванов. Пенза – 2018 г. Издательство АО «Пензенский научно-исследовательский электротехнический институт» (АО «ПНИЭИ») – 27 с.
Список литературы на английском языке / References in English
- Krylova, I. Yu. Biometricheskie tehnologii kak mehanizm obespechenija informacionnoj bezopasnosti v cifrovoj jekonomike [Biometric technologies as a mechanism for ensuring information security in the digital economy] / I. Yu. Krylova, O.S. Rudakova // Young scientist. - 2018. - No. 45 (231). - P. 74-79. [in Russian]
- GOST R 52633.5-2011. Zashhita informacii. Tehnika zashhity informacii.Avtomaticheskoe nejrosetevyh preobrazovatelej biometrija-kod dostupa [GOST R 52633.5-2011. Information protection. Information protection technology. The neural net biometrics-code converter automatic training]. Moscow: Standartinform Publisher, 2011. [in Russian]
- Tret'e pokolenie nejrosetej: "Glubokie nejroseti" [The third generation of neural networks: "Deep neural networks"] - [Electronic resource]. URL: https://www.mql5.com/ru/articles/1103 (accessed: 05/10/2021). [in Russian]
- Kolmogorov A.N. O predstavlenii nepreryvnyh funkcij neskol'kih peremennyh v vide superpozicii nepreryvnyh funkcij odnogo peremennogo [On the representation of continuous functions of a number in the form of a superposition of continuous functions of one variable] / A.N. Kolmogorov // AN SSSR [Dokl. Academy of Sciences of the USSR]. 1957. No. 5 (114). P. 953–956. [in Russian]
- Serikova Yu. I. Aktual'nye problemy bezopasnosti biometricheskih sistem autentifikacii [Actual problems of biometric authentication systems security] / Yu. I. Serikova, VN Knyazev // Mezhdunarodnyj nauchno-issledovatel'skij zhurnal [International research journal]. - 2016. - No. 4 (46) Part 2. - P. 177-182. - DOI: 10.18454 / IRJ.2016.46.105. [in Russian]
- Ivanov A.I. Chislennaja ocenka pokazatelej kvantovoj sceplennosti vyhodnyh kubit nejrosetevoj molekuly preobrazovatelja biometricheskih dannyh [Numerical estimation of the parameters of the quantum entanglement of the output qubits of the neural network molecule of the biometric data converter] / A.I. Ivanov. Penza - 2018 Publishing house of JSC «Penza Scientific Research Electrotechnical Institute» (JSC «PNIEI») - 27 p. [in Russian]