АНАЛИЗ ГОСУДАРСТВЕННОГО СТАНДАРТА ШИФРОВАНИЯ РОССИИ ГОСТ 28147-89 С ЦЕЛЬЮ ЕГО ИНТЕГРАЦИИ В ИНФОКОММУНИКАЦИОННЫЕ СТРУКТУРЫ БОЛИВАРИАНСКОЙ РЕСПУБЛИКИ ВЕНЕСУЭЛА
Санчес Россель Хосе Агустин
Аспирант, Института компьютерных технологий и информационной безопасности ФГАОУ ВПО «Южный Федеральный Университет»
АНАЛИЗ ГОСУДАРСТВЕННОГО СТАНДАРТА ШИФРОВАНИЯ РОССИИ ГОСТ 28147-89 С ЦЕЛЬЮ ЕГО ИНТЕГРАЦИИ В ИНФОКОММУНИКАЦИОННЫЕ СТРУКТУРЫ БОЛИВАРИАНСКОЙ РЕСПУБЛИКИ ВЕНЕСУЭЛА
Аннотация
В статье рассмотрен алгоритм криптографических преобразований ГОСТ 28147-89, используемый в настоящий момент в Российской Федераци, который регламентирует ряд действий шифрования, а так же построенного на смежных принципах алгоритма выработки имитовставики. Проанализирована возможность его интеграции винфокоммуникационные структуры Боливарианской Республики Венесуэла.
Ключевые сова: алгоритм криптографической защиты, имитовставка, блочные шифры, симметричное шифрование, ГОСТ 28147-89.
Sanchez Rossel Jose Agustin
Postgaduate student FSAEI HPO «South Federal University»
ANALYSIS OF PUBLIC ENCRYPTION STANDARD RUSSIAN GOST 28147-89 WITH A VIEW TO ITS INTEGRATION IN INFORMATION AND COMMUNICATION PATTERNS OF THE BOLIVARIAN REPUBLIC OF VENEZUELA
Abstract
The article describes the cryptographic algorithm GOST 28147-89, currently in use in the Russian Federation, which regulates a number of actions encryption and built on related principles of the algorithm generate interpretation. Analyzed the possibility of its integration in information and communication patterns of the Bolivarian Republic of Venezuela.
Keywords: cryptographic algorithm for the protection, interpretation, block ciphers, symmetric encryption, GOST 28147-89.
Security of information and communication structures in the moment is one of the most important tasks of any state, along with the country's defense, health, economy and education.
Information security is organized with the help of cryptographic systems, i.e. using sets of cryptographic transformations or algorithms designed to operate in a single technological chain with the purpose of solving a specific task of protection of the information process. Their implementation uses cryptographic functions, which include: a key generators, encryption functions, pseudorandom generators, calculation and verification of the code values of the authenticity of the message and the digital signature, the value computation of the hash function and others. The present article is devoted to the analysis of cryptographic algorithms GOST 28147-89 (hereinafter simply GOST).
Description of the algorithm GOST
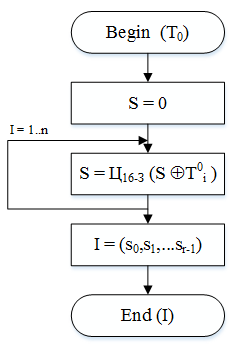
GOST refers to the standard symmetric encryption used in the Russian Federation since 1990 This standard describes a number of actions encryption and built on related principles of the algorithm generate interpretation (fig. 1) [1].
Authentication code is a segment of fixed length information obtained by a specific rule of open data and key and added to the encrypted data to ensure the protection of the encrypted communication system from imposing false data (prevention of false data entry).
The symmetric encryption has the following requirements:
- the lack of linearity (i.e. f(a)xor f(b)=f(a xor b), otherwise facilitates the application of differential cryptanalysis of the cipher);
- complete loss of all statistical laws of amerista original message (cipher must have the "avalanche effect").
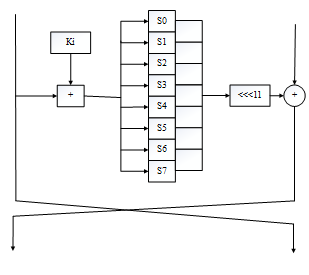
The algorithm GOST is a data encryption 64-bit blocks using a key consisting of 256 bits. In the process of encryption takes place 32 round of transformation (Fig. 2):
- One of the sub-blocks of data of 32-bit size is summed with the value of the 32-bit key encryption round (by │232│).
- The result is broken into eight 4-bit parts, which at the same time pass through eight of substitution tables .
- Parts again after the substitutions are combined into a 32-bit subunit. Then the value of subunit cyclically shifted by 11 bits.
- Next, after the operations described above, the subunit is superimposed on the raw by using the bitwise logical "exclusive or" (XOR).
- Ultimately, the subunits are swapped.
Fig. 1 - The algorithm of generation interpretation for data array
Fig. 2 - Round algorithm GOST 28147-89
Unlike most of the encryption algorithms GOST can use any variations of the blocks, as it has no fixed block replacement.
Classical block ciphers, including GOST, built on the principle of zero, that is, the secrecy of the key determines the secrecy of encrypted messages, so the resistance of such codes depends on the size of the used key. In the Guest uses 256-bit key and volume key space is 2^256. Secret 256-bit encryption key is represented as a sequence of eight 32-bit words (K1, K2, K3, K4, K5, K6, K7, K8). One of these eight words in each round of encryption is used as roundabo changed. Round key is defined as follows: 1 through 24 rounds are used sequentially K1, K2, K3, K4, K5, K6, K7, K8, K1, K2, etc., and from 25 to 32 rounds: K8, K7, K6, K5, K4, K3, K2, K1.
As we can see from the description, the algorithm GOST is quite simple to implement. In addition to the advantages of GOST can be attributed:
- the futility of force exhaustive search attack;
- efficient implementation on modern computers;
- protection against the imposition of false data (generation of the authentication code) and the same encryption round in all four algorithms GOST.
The disadvantage of GOST is the incompleteness of the standard in question generate keys and replacement tables. A trivial way to prove the existence of weak keys and replacement tables, but the standard does not include information about selection criteria and screening "weak".
Cryptanalysis of the algorithm
Today, you can find only a small number of works devoted to the analysis of cryptographic strength of the algorithm GOST, unlike encryption standards DES and AES.
One of the first public works, which was the analysis of the algorithm [2], shows that ponoramnoy algorithm GOST 28147-89 can be opened using differential cryptanalysis, related, but only in the case of weak replacement tables. In studies L. K. Babenko and E. A. Ishukova is an algorithm of searching for weak units [3, 4]. Application of this algorithm makes it easy to detect a large number of weakened replacement blocks, which can significantly weaken the resistance of the used encryption algorithm. Thus, the use of strong replacement tables found this algorithm for doing such an attack completely impractical.
In [5] is performed cryptanalysis modifications of the algorithm GOST 28147-89 (GOST-H and GOSTÅ). The analysis shows that the algorithms GOST-H and GOSTÅ weaker than the classical algorithm GOST 28147-89, since both classes have weak keys.
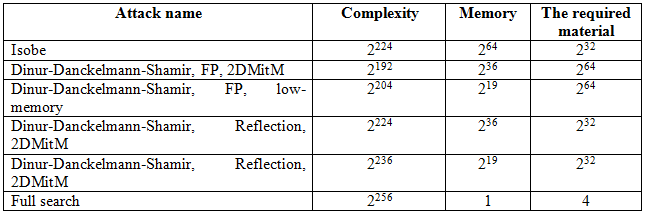
Below is information about all the known results strictly described attacks on GOST 28147-89 (table 1).
Table 1
As can be seen from the data, while meeting current operational requirements, none of the proposed methods of cryptanalysis of GOST 28147-89 is not possible to determine the key with lesser complexity of exhaustive search.
The above mentioned studies and several other studies [6-7] allow to conclude that a sufficiently high strength of Russian algorithm cryptographic protection.
Conclusions
Analysis of public encryption standard, Russian GOST 28147-89 shows that, regardless of age (as the state standard it is registered in 1989), algorithms GOST easy to use, still have considerable cryptographic strength and high efficiency.
Thus, to improve the effectiveness of information security of the Bolivarian Republic of Venezuela, it seems appropriate to integrate the algorithms GOST in information and communication structures of the state.
References
- GOST 28147-89 System of information processing. The cryptographic protection. Cryptographic transformation algorithm – М.: Gosstandart of the USSR, 1989.
- Kelsey J., Schneier B., Wagner D. Key-Schedule Cryptanalysis of IDEA, G-DES, GOST, SAFER, and Triple-DES. //http://www.schneier.com– 1996.
- Babenko L.K., Ishukova Е.А. The analysis of the algorithm GOST 28147-89: the search for weak units // News SFU. Technical science. Thematic issue on "Information security”. – Taganrog: Изд-во ТТИ ЮФУ. – 2014. – № 2(151) – С. 148–157.
- Babenko L.K., Ishukova Е.А. Использование слабых блоков замены для линейного криптоанализа блочных шифров // News SFU. Technical science. Thematic issue on "Information security”. – Taganrog: Изд-во ТТИ ЮФУ. – 2014. – № 2(151). – С. 136–147.
- Oreku G.S., Li J., Pazynyuk T., Mtenzi F.J. Modified S-box to Archive Accelerated GOST. //http://paper.ijcsns.org – International Journal of Computer Science and Network Security, VOL. 7 No. 6, June 2007.
- Schneier B. Applied cryptography. Protocols, algorithms, and source code in C language. – trans. fron eng.: М.: Publisher ТРИУМФ, 2002 – 816 с.
- Rostovtsev, A. G., Makhovenko E. B., Phillipov A. C., A. Chechulin, A. On the strength of GOST 28147-89. //http://www.ssl.stu.neva.ru– СПбГПУ.
- Oreku G.S., Li J., Pazynyuk T., Mtenzi F.J. Modified S-box to Archive Accelerated GOST. //http://paper.ijcsns.org– International Journal of Computer Science and Network Security, VOL. 7 No. 6, June 2007